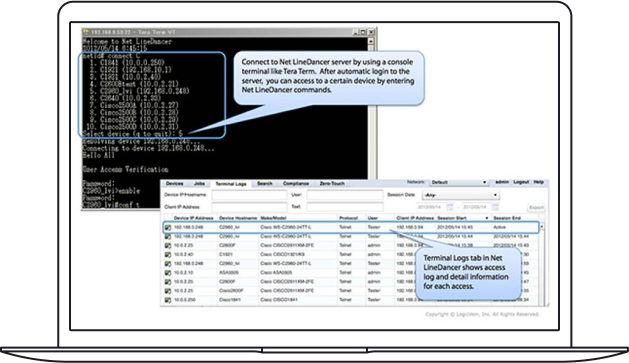
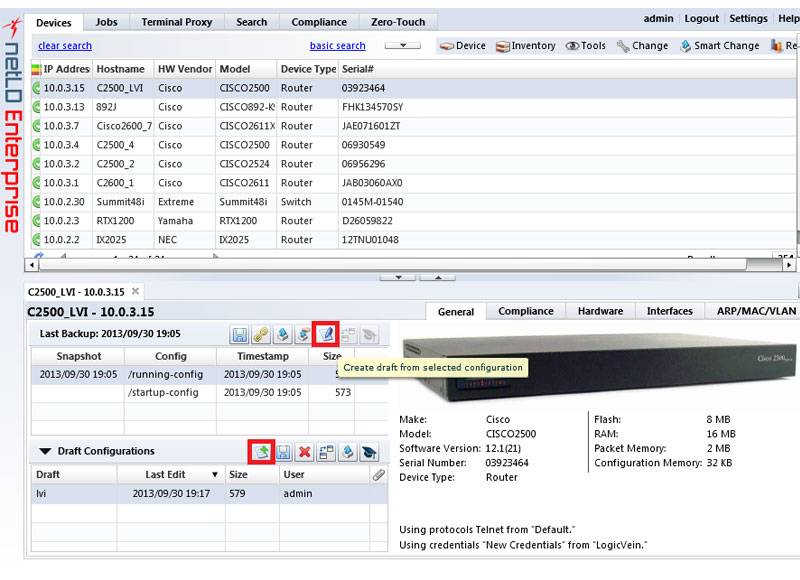
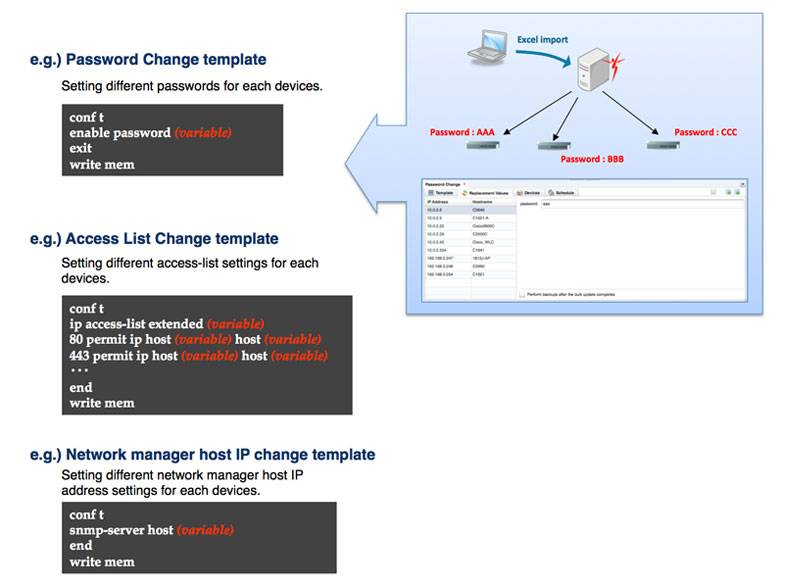
What Can Our Network Configuration Management Software Do for You?
Your digital infrastructure is constantly evolving and expanding, so keeping it secure and resilient is a monumental task.
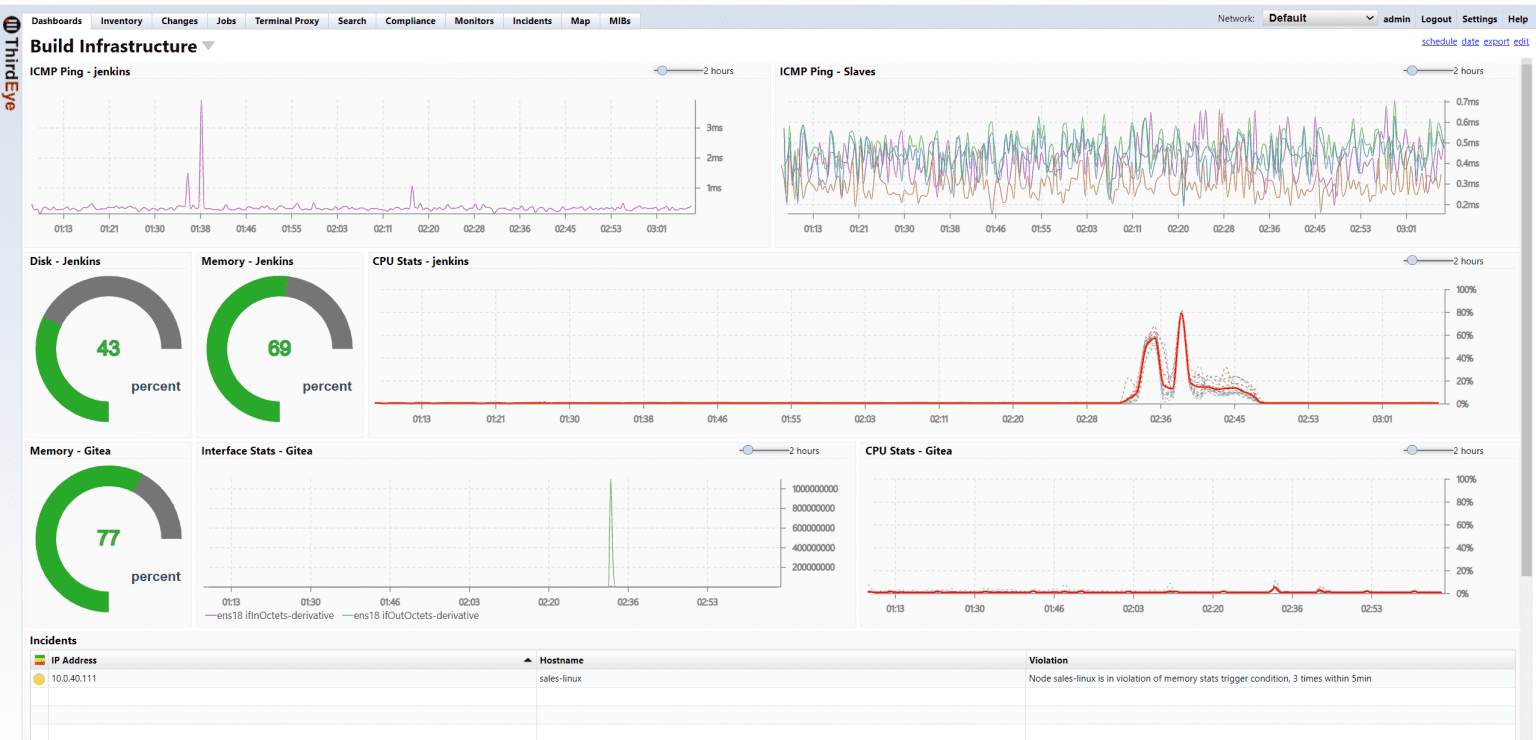
ThirdEye provides a new level of awareness, integrating high-fidelity performance monitoring with deep configuration control.
We designed ThirdEye to move your team beyond reactive problem-solving to truly effective configuration management,
empowering you with the foresight and tools to master your network's complexity.
Illuminate Your Full Network Inventory
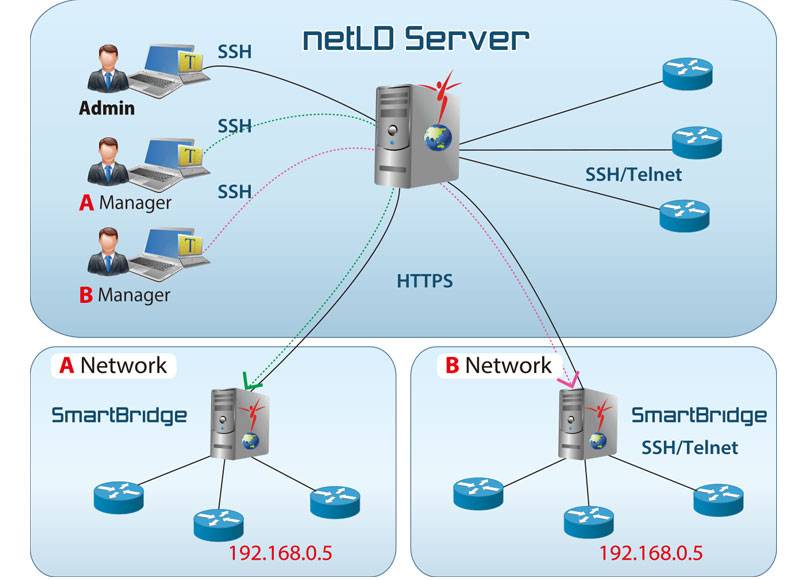
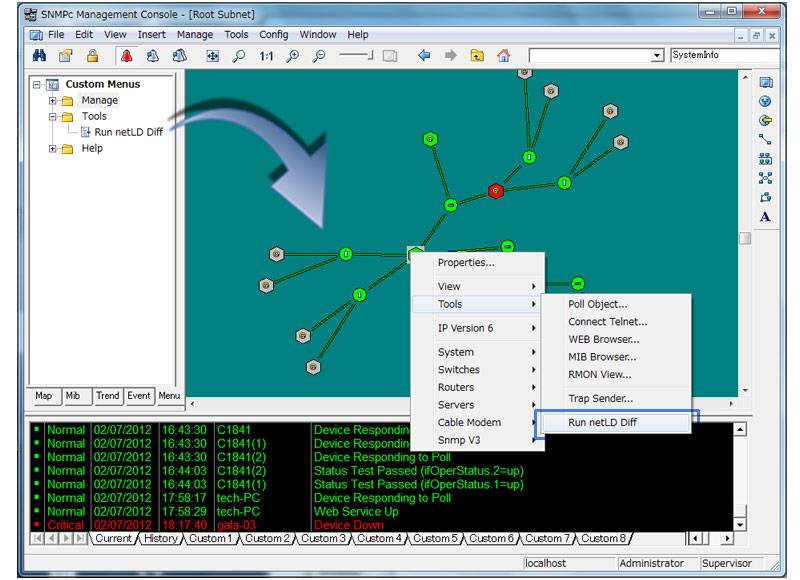
A sprawling inventory of unknown hardware presents constant operational risk. ThirdEye automatically explores every connection
to build a living map of your assets. Use it as the command center for firmware management, instantly identify outdated versions,
and deploy targeted updates with precision.
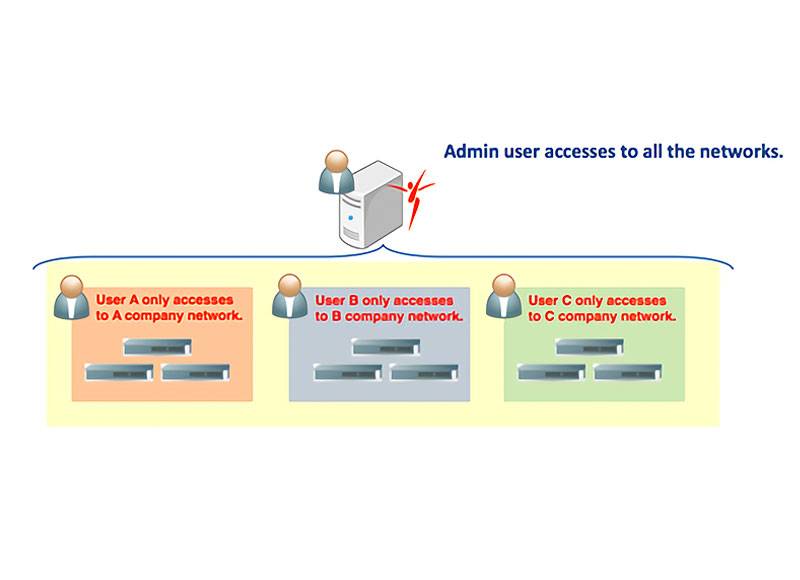
Develop a Proactive Security Immune System
ThirdEye’s vulnerability management continuously scans configurations to identify weaknesses before they become attack vectors.
Enforce smart security policies and transform your posture from passive to proactive.
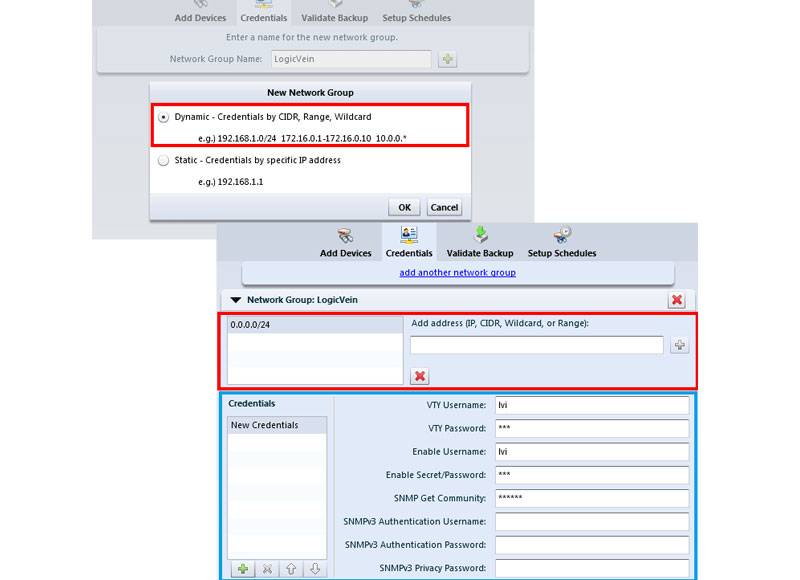
Master Policy Compliance with Automated Certainty
ThirdEye continuously monitors configurations against internal benchmarks and external regulations. Generate detailed, on-demand reports
that prove compliance and document configuration history.
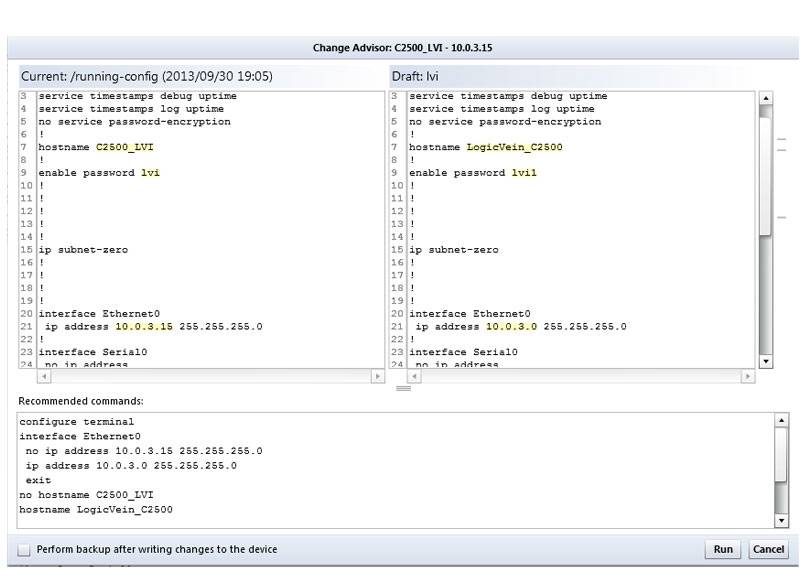
Engineer Away Configuration Errors
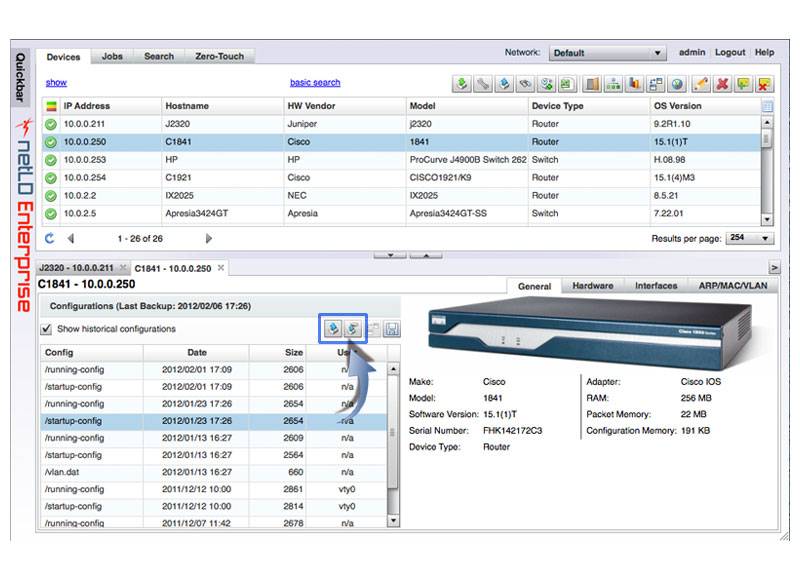
Validate changes against preset rules to catch errors before they impact production. With versioned backups of every device,
you can reverse mistakes instantly.
Forge True Network Resilience and Continuity
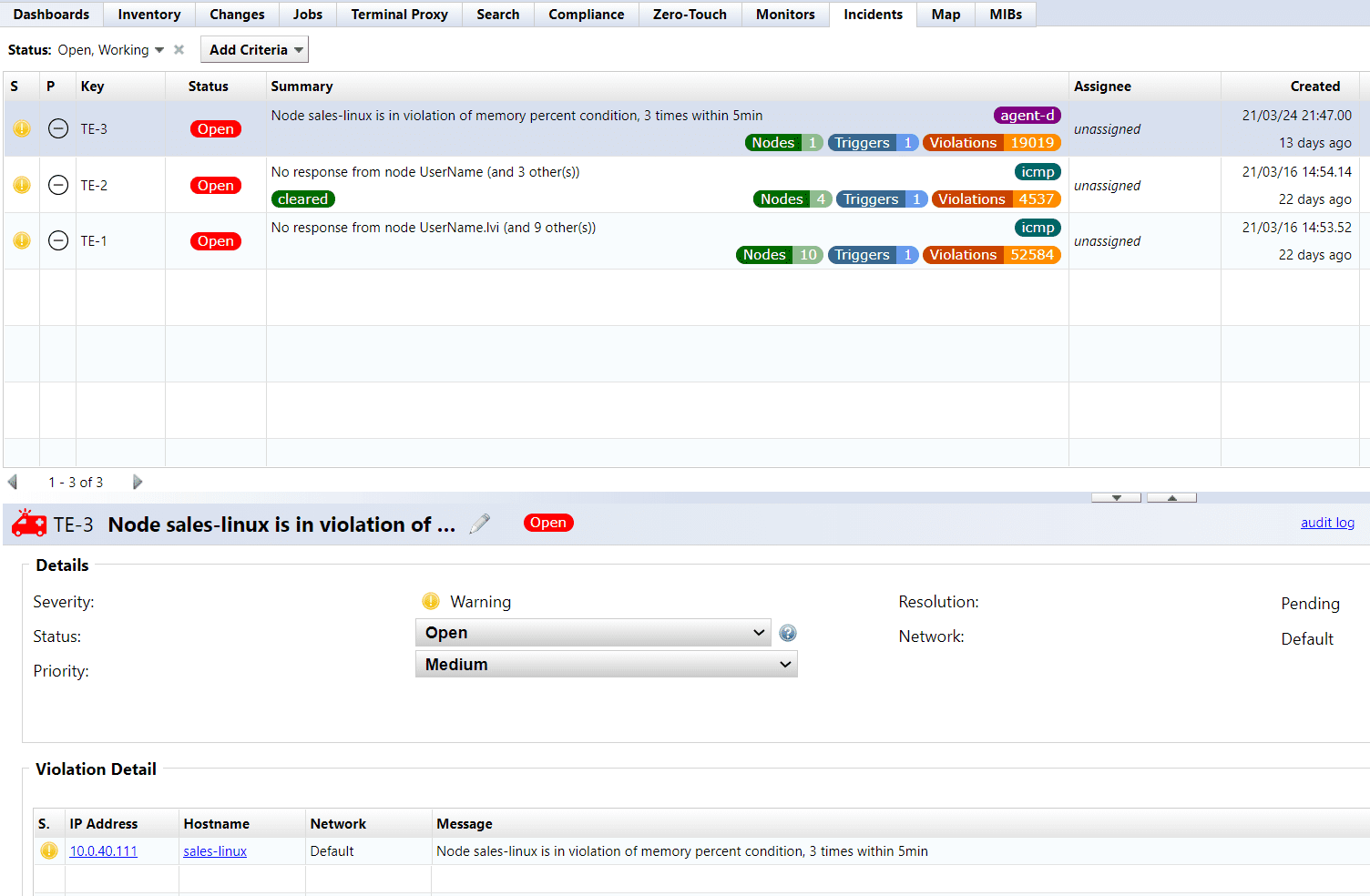
In an incident, a complete, timestamped change history exposes root causes fast. Perform targeted rollbacks of the exact modification
that introduced the issue and minimize downtime.
Correlate performance metrics with the configuration timeline to see precisely when a dip occurred and link it to the change that caused it.
Ready to adopt best practices? Start your free 30-day trial today.